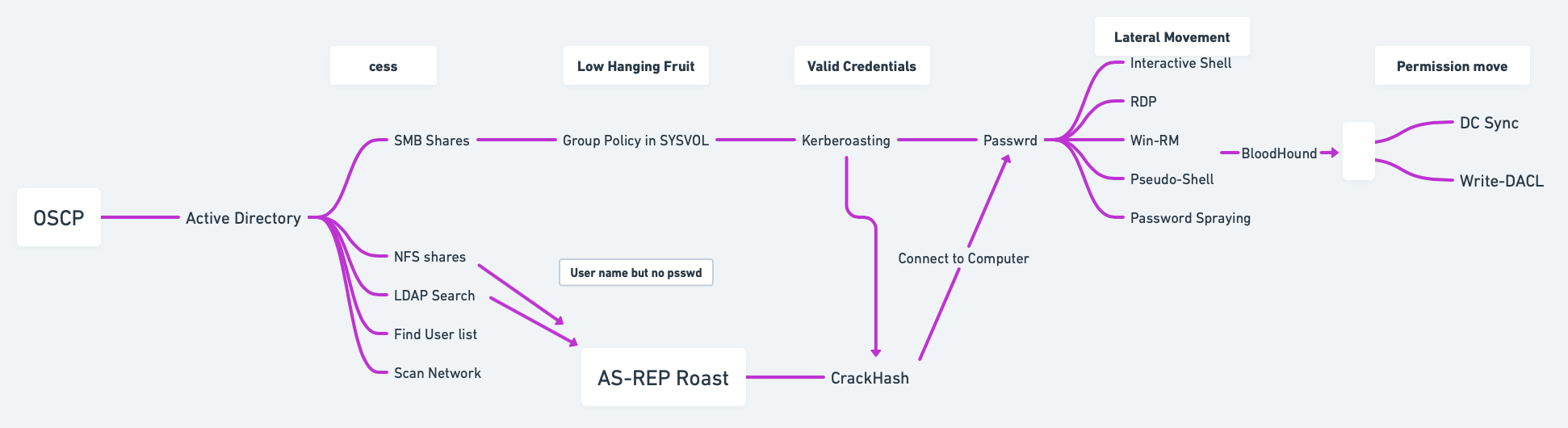
🕵️Active Directory Cheat Sheet
1. 📜 Active Directory Theory
1.1 Overview
Active Directory (AD) manages objects (e.g., computers, users) in a domain, such as
domain.com, and organizes them into Organizational Units (OUs).Domain Controllers (DCs) store all the password hashes for domain users.
To control AD fully, target the Domain Admins group or a Domain Controller.
Services like Exchange or IIS integrate with AD using Service Principal Names (SPNs), which identify services and link them to service accounts.
Kerberos is used to authenticate users and services using tickets, and if I have an user's ticket I can impersonate that user.
1.2 Authentication
NTLM: Uses a challenge/response protocol to authenticate users without transmitting passwords.
Kerberos: Relies on a Key Distribution Center (KDC) to issue Ticket Granting Tickets (TGTs) and Service Tickets (TGSs) for user authentication.
TGT: Provides authentication validity for up to 10 hours, and a session key for accessing domain resources.
TGS: Allows users to access services using SPNs, with permissions granted based on group membership.
1.3 Credential Storage & Hash Dumping
LSASS stores password hashes for single sign-on (SSO). With admin access, tools like Mimikatz can dump:
Password hashes.
TGTs and TGSs (for Kerberoasting or forgery).
Kerberoasting: Crack the service account’s password hash from TGS tickets to reveal the clear-text password.
Silver/Golden Tickets: Forging TGS tickets using cracked SPN password hashes to impersonate users.
1.4 Common Attack Vectors
AS-REP Roasting: Target accounts without Kerberos Pre-Authentication (indicated by the
DONT_REQ_PREAUTHflag), extract AS-REP responses, and attempt to crack the encrypted part offline.Kerberoasting: Target SPNs, extract TGS tickets, crack the passwords offline.
Pass-the-Hash (PtH): Reuse NTLM hashes to authenticate to services without cracking the password.
Pass-the-Ticket (PtT): Use stolen Kerberos tickets to move laterally or maintain persistence.
Silver Ticket: Enables attackers to forge a TGS ticket for a specific service using the NTLM hash of the service account. This allows unauthorized access to that service without needing user credentials.
Golden Ticket: Allows attackers to forge a TGT using the KRBTGT account hash, enabling them to impersonate any user in the domain, including privileged accounts, and gain extensive access across the network.
Kerberos Delegation Abuse:
Unconstrained Delegation: Allows attackers to impersonate any user, including privileged ones, by using a high-privileged TGT.
Constrained Delegation: Allows impersonation of specific users for services where delegation has been configured; so restricts the impersonation capabilities to specific services.
DC Sync: Allows attackers with certain privileges (e.g., Replicating Directory Changes) to impersonate a Domain Controller and request password hashes, including NTLM hashes, from the AD; the user needs the permissions
DC-Replication-Get-Changesalong with the privilege GetChangesAll.
1.5 Lateral Movement
Pass the Hash (PtH): Use NTLM hashes to authenticate to remote systems without needing the plaintext password.
Overpass the Hash: Use an NTLM hash to request a TGT for Kerberos-based services, enabling domain-wide movement without the need for the actual password.
1.6 Persistence
Golden Ticket Attack: By obtaining the krbtgt password hash, an attacker can forge TGTs and impersonate any user.
DCSync Attack: Request replication updates from DCs to retrieve password hashes of every AD user.
12. 🕵️♂️ Active Directory Enumeration
12.1 Initial Recon with Nmap
Start by scanning the target with Nmap to identify potential services and domain controllers (DC):
Common Active Directory ports:
53: DNS
88: Kerberos
135: RPC
139/445: SMB
389/636: LDAP/LDAPS
464: Kerberos Password Change
5985: WinRM
Recommended Strategy:
Perform LDAP Search: retrieve potential user and password information.
Enumerate DNS: gather information about key servers within the domain.
Enumerate LDAP Services:
Find Valid Users:
Enumerate All AD Users: this has to be done after having valid credentials.
2.1.1 DNS Enumeration (Port 53)
Nmap Scripting Scan
Enumerating AD Domain via DNS
Zone Transfer: test for DNS zone transfer to retrieve a list of domain records.
DNS Record Lookup: query specific domain records, such as domain controllers and mail servers.
Basic DNS Enumeration
Zone Transfer
Reverse Lookup
DNS Cache Snooping
Enumerate DNS with PowerShell (Windows)
2.1.2 Kerberos Enumeration (Port 88)
Nmap Scripting Scan
AS-REP Roasting: extract accounts with pre-authentication disabled using GetNPUsers.py (impacket-GetNPUsers); keep in mind that should also use kerbrute to find possible valid usernames, commands for this are in the Section 1.4.7.
Kerberoasting: use GetUserSPNs.py to extract SPNs.
Enumerate Kerberos Principal Names: use kerbrute to enumerate valid user accounts by attempting to authenticate with a list of usernames.
Perform Kerberos Ticket Extraction (AS-REP Roasting): request non-preauthenticated Kerberos tickets for a list of users.
Perform Kerberos Ticket Request with AS-REP Roasting: request a Ticket Granting Ticket (TGT) for a specific user.
Crack Kerberos Tickets
Kerberos Ticket Extraction: request a TGT or Service Ticket (TGS) using specified credentials.
Kerberoasting: extract and crack service tickets to gain access to service accounts.
Kerberos Brute Forcing: perform brute force attacks on Kerberos tickets.
Kerberos Ticket Manipulation: use tools to request, manipulate, and renew Kerberos tickets for privilege escalation or impersonation.
Kerberos Ticket Dumping: extract Kerberos tickets from memory for offline analysis.
Kerberos Pre-Authentication: identify weak configurations that might allow attackers to perform brute force attacks.
Kerberos Silver Ticket Attacks: forge high-value Kerberos tickets for access and privilege escalation.
Steps to Perform Silver Ticket Attack
Kerberos Golden Ticket Attacks: forge high-value Kerberos tickets for access and privilege escalation.
Steps to Perform Golden Ticket Attack
Additional Reference: https://www.tarlogic.com/blog/how-to-attack-kerberos/
2.1.3 LDAP Enumeration (Port 389/636)
Nmap Scripting Scan
Basic LDAP Search: query the LDAP service for domain information
Extract AD Users and Groups
Ldapsearch Basic Enumeration
Check Pre-Authentication for Users
Useful Search Terms
2.1.4 SMB/NetBIOS Enumeration (Port 445)
Host Enumeration
Nmap Scripting Scan
SMB Shares Enumeration
Enumerate Users
Advanced Enumeration
SMB Enumeration with smbmap
SMB Enumeration with crackmapexec
User Enumeration with enum4linux
SMB Client Operations
Brute Force Credentials
Mounting Shares
Execute Remote Commands
Exploitation (EternalBlue - MS17-010): https://github.com/3ndG4me/AutoBlue-MS17-010
PsExec
WMIExec
2.1.5 WinRM Enumeration and Access (Port 5985)
Nmap Scripting Scan
Test WinRM Access: use CME to test if WinRM is enabled:
WinRM Login with Evil-WinRM: if valid credentials are found, log in via Evil-WinRM:
Crackmapexec
Loggin In
2.2 Basic Enumeration
Recommended Methodology:
Find my Domain SID:
Find the name of my domain controller server:
Find Service Account Names:
Finding SPNs:
Check users of the domain:
Check groups of the domain:
Script to get the full LDAP path:
Script to get full information for SAM account types:
Enumerate nested groups with custom LDAP query:
Encapsulate LDAP search into a function:
Perform user search using LDAP query:
Search for all possible groups in AD:
Iterate through objects in
$groupvariable:
2.3 PowerView
Import PowerView (ensure it is downloaded first):
Domain information:
Find Domain Name
Get Domain User
Users information:
Groups information:
Operating System information:
Get Domain Admins
Find Kerberoastable Accounts
Enumerate Domain Controllers
Find Shares
Check for Delegation
2.4 Service Principal Names (SPN) Enumeration
List SPN linked to a user:
List SPN accounts in the domain:
2.5 Object Permissions Enumeration
Active Directory permission types:
GenericAll: Full permissionsGenericWrite: Edit certain attributesWriteOwner: Change ownershipWriteDACL: Edit ACEs appliedAllExtendedRights: Change/reset password, etc.ForceChangePassword: Force password changeSelf: Add self to groups
Run
Get-ObjectAcl(PowerView) to specify user:
Convert Object SID to a name:
Enumerate ACLs for a group:
Convert SIDs with GenericAll permission to names:
Add yourself to a domain group:
Verify group membership:
2.6 Domain Shares Enumeration
Find domain shares (PowerView):
Decrypt GPP password using gpp-decrypt:
2.7 BloodHound & SharpHound
BloodHound is a tool for Active Directory (AD) enumeration and privilege escalation, designed to help visualize AD relationships and identify paths for lateral movement and privilege escalation.
Resources:
Download and Transfer SharpHound:
Running SharpHound
Find your Domain Name:
Using the PowerShell Script:
Collect Specific Methods: run only specific collection tasks instead of
Allto limit the data gathered.
Transfer Collected Data to Kali: once SharpHound finishes collecting, transfer the output
.zipfile fromC:\Tempback to your Kali machine. You can use one of the methods below or check Section 15 for additional transfer methods.
Running BloodHound on Kali: access the Neo4j interface at
https://localhost:7474and log in with default credentialsneo4j:neo4jorneo4j:Neo4j.
Start BloodHound:
Import the .zip files collected from the victim machine into BloodHound for analysis.
Analyze the domain data:
Use queries like Find all Domain Admins or Find Shortest Paths to Domain Admins.
Find computers vulnerable to Unconstrained Delegation.
Mark nodes as owned to find potential escalation paths.
Set Node Label Display to Always Display in the settings for better visibility.
Identify Kerberoastable accounts.
Find potential GPOs to abuse: if BloodHound indicates that a user or group has
WriteGPO,OwnsGPO, orGPO controlover a GPO linked to important OUs (especially those affecting privileged accounts), this is a strong indicator to use SharpGPOAbuse to escalate privileges or perform lateral movement.
Manual Commands:
Format for cypher:
(NODES)-[:RELATIONSHIP]->(NODES)All computers in domain:
MATCH (m:Computer) RETURN mAll Users in domain:
MATCH (m:User) RETURN mGet active sessions:
MATCH p = (c:Computer)-[:HasSession]->(m:User) RETURN pEnumerate users with
SQLAdmin:MATCH p1=shortestPath((u1:User)-[r1:MemberOf*1..]->(g1:Group)) MATCH p2=(u1)-[:SQLAdmin*1..]->(c:Computer) RETURN p2Enumerate users with
CanPSRemote:MATCH p1=shortestPath((u1:User)-[r1:MemberOf*1..]->(g1:Group)) MATCH p2=(u1)-[:CanPSRemote*1..]->(c:Computer) RETURN p2
2.8 Extracting and Cracking Password Hashes
Dump Hashes with SecretsDump: use SecretsDump to extract NTDS.dit or password hashes.
Crack NTLM Hashes: once you have the hashes, crack them with Hashcat or John the Ripper.
Password Spraying: involves testing common passwords across many accounts to avoid account lockouts. CrackMapExec is ideal for this.
2.9 MS-RPRN Print Spooler Service Exploitation
The Print Spooler service has been linked to critical vulnerabilities, notably CVE-2021-34527 (PrintNightmare). This vulnerability allows attackers to execute arbitrary code remotely with SYSTEM privileges due to improper handling of requests.
Enumerate Printers: if Print Spooler service is enabled, enumerate available printers.
2.10 Common SPNs for Service Accounts
cifs
Common Internet File System
dcom
Distributed Component Object Model
exchange
Microsoft Exchange Server
ftp
File Transfer Protocol
http
Hypertext Transfer Protocol
imap
Internet Message Access Protocol
krbtgt
Kerberos Ticket Granting Ticket
ldap
Lightweight Directory Access Protocol
mssql
Microsoft SQL Server
mysql
MySQL Database
nfs
Network File System
oracle
Oracle Database
pgsq
PostgreSQL Database
pop3
Post Office Protocol 3
rpc
Remote Procedure Call
smtp
Simple Mail Transfer Protocol
svc
Service
termsrv
Terminal Server
wsman
Windows Remote Management
2.11 GPP Passwords Abuse (Group Policy Preferences)
2.11.1 GPP Main Method for Extraction
Search for GPP Passwords in SYSVOL: access SYSVOL share and search for Group Policy Preferences (GPP) files; this happens because a common useful misconfiguration found in modern domain environments is unprotected Windows GPP settings files
Map the DC SYSVOL share:
Find the GPP file: usually the one called
Groups.xml: the file is usually located in a path similar to this one\hostname.domain\Policies\{00000000–0000–0000–0000–00000000000}\MACHINE\Preferences\Groups\Groups.xml.
Decrypt the Found
Hash/cpassword:
(Optional) Alternative Method:
2.11.2 Impacket-Get-GPPPassword
Impacket-Get-GPPPassword (Get-GPPPassword.py) is an Impacket script for retrieving GPP passwords. There are several methods for using this script depending on the level of access you have:
NULL Session: this command attempts to retrieve GPP passwords without providing any credentials (NULL session). Useful if anonymous access is allowed on the target Domain Controller (DC).
With Cleartext Credentials: uses cleartext credentials (username and password) to access and retrieve stored GPP passwords from the DC.
Pass-the-Hash (with NT hash): executes a pass-the-hash attack with the user’s NTLM hash instead of a password, allowing retrieval of GPP passwords.
Parsing a Local File: this command parses a local Policy XML file for stored passwords. Useful if you have a downloaded or extracted policy file on your machine.
2.11.3 SMB Share-SYSVOL
SYSVOL is a shared folder on the DC where Group Policy objects (GPOs) and scripts are stored. This folder is often accessible to any domain user, allowing attackers to potentially access configuration files with stored passwords (GPP).
Download the Entire Share: you can use a tool or script to download the entire SYSVOL share for offline analysis.
Navigate to Downloaded Files: this command searches through the downloaded files for instances of
cpassword(encrypted passwords stored in the XML files), helping identify where passwords are stored.
2.11.4 CrackMapExec
CrackMapExec is a popular tool for SMB enumeration and exploitation. Here, it is used to locate GPP passwords.
With Username and Password: this command scans one or multiple targets to identify stored GPP passwords using cleartext credentials.
With NTLM Hash: this variant allows pass-the-hash authentication with NT and LM hashes instead of a password.
2.12 Scripts (adPEAS)
2.12.1 Importing the Module
Download from https://github.com/61106960/adPEAS?tab=readme-ov-file#important-note-about-the-bloodhound-module.
2.12.2 Basic Usage
Enumerate Current Domain: start adPEAS and enumerate the domain for the logged-on user and computer.
Specify Domain and Output: to specify a domain and save output without ANSI color codes.
Specify Domain Controller: to enumerate using a specific domain controller.
Using PSCredential: to use a PSCredential object for enumeration.
Force Enumeration with Username and Password: to specify username and password for enumeration while ignoring DNS issues.
2.12.3 Module-Specific Usage
Basic Active Directory Information
Active Directory Rights and Permissions
Group Policy Information
Active Directory Certificate Services Information
Credential Exposure Issues
Delegation Issues
High Privileged Groups Enumeration
Domain Controller and Service Enumeration
BloodHound Enumeration (DCOnly)
BloodHound Enumeration (All)
2.13 Group Managed Service Accounts (gMSAs) Abuse
2.13.1 Identifying Group Managed Service Accounts (gMSAs)
2.13.1.1 Manual Discovery of gMSAs
You can manually search for gMSA accounts in Active Directory using PowerShell or LDAP queries.
Using PowerShell PowerShell’s Get-ADServiceAccount cmdlet can help identify gMSA accounts, assuming you have sufficient permissions. This command lists all gMSAs in the domain with their properties, including msDS-ManagedPassword, if you have permissions to view it.
Using LDAP Query You can also search for gMSAs directly by filtering based on their object class. This approach is useful if you don’t have access to Get-ADServiceAccount but can execute LDAP queries. You can inspect the properties of each returned object for further information, like the account's service name.
Identify Accessible gMSA Passwords: Once gMSAs are identified, check if you can read the msDS-ManagedPassword attribute. This attribute contains the encrypted password and is often readable by specific privileged accounts or groups.
2.13.1.2 Automated Discovery with BloodHound
BloodHound can map out relationships and permissions in Active Directory, making it ideal for identifying exploitable accounts, including gMSAs.
Run BloodHound Collection: use BloodHound’s
SharpHoundcollector to gather data from the domain.
Analyze in BloodHound GUI: open the BloodHound GUI, upload the collected data, and search for accounts with privileges to read gMSA passwords:
Use the "Find Principals with DCSync Rights" query, which might help indirectly as gMSA permissions are often linked to elevated roles.
Search for any objects where specific user groups have
ReadPropertyrights on themsDS-ManagedPasswordattribute.
(Optional) Query Examples in BloodHound:
Use the query
Find Principals with Unusual Rights on Password Attributes, as this often includes gMSA password attributes.BloodHound may highlight gMSA accounts that are configured with permissions for non-admin users or groups, indicating potential targets for exploitation.
2.13.2 GMSA Password Retrieval with GMSAPasswordReader
GMSAPasswordReader.exe can be used to retrieve the plaintext password for Group Managed Service Accounts (gMSAs). This tool requires specific permissions, usually access to read the msDS-ManagedPassword attribute of the gMSA object.
2.13.2.1 Usage
Run
GMSAPasswordReader.exewith Proper Privileges: ensure you have sufficient permissions to read gMSA password attributes in Active Directory. Typically, Domain Admin or specific permissions on the gMSA object are required.Command Syntax: the tool can be run from the command line to retrieve gMSA passwords.
2.13.2.2 Additional Notes
Permissions: Ensure that you have necessary read permissions on the
msDS-ManagedPasswordattribute.Privileged Access: Typically, this tool is most useful on systems where you already have Domain Admin or specific delegated permissions on gMSA objects.
Security Considerations: Use this tool carefully, as improper handling of retrieved passwords can expose sensitive credentials.
2.13.3 Alternative Commands
If you don’t have access to GMSAPasswordReader.exe, you might consider using PowerShell or other Active Directory enumeration techniques if you have appropriate permissions to query gMSA accounts and their attributes.
Using PowerShell with Active Directory Module: if you have the Active Directory PowerShell module installed, you can use it to query for gMSAs and their
msDS-ManagedPasswordattribute. This command lists all gMSAs and attempts to retrieve theirmsDS-ManagedPasswordattribute. You need permissions to read this attribute.
Using
Get-ADObjectto Directly Query LDAP Attributes: ifGet-ADServiceAccountisn’t available,Get-ADObjectcan directly query Active Directory for objects withmsDS-ManagedPassword. This command retrieves all gMSA objects, showing their attributes, including the managed password (if accessible).
Retrieving gMSA Passwords with
Get-ADAttributeEditor: if you have permissions and access to the Active Directory UI on a Windows machine; if you have read permissions, you should be able to view or export the password attribute here.Open the Active Directory Users and Computers console.
Enable Advanced Features (under View).
Locate the gMSA account, right-click, and select Properties.
Navigate to the Attribute Editor tab and search for
msDS-ManagedPassword.
Using LDAP Queries with
ldapsearch(Linux): if you’re on a Linux system with ldapsearch installed, you can use it to query Active Directory for gMSA accounts. This approach requires credentials with LDAP access. This command fetches gMSA objects and tries to access themsDS-ManagedPasswordattribute.
PowerView: if you’re using PowerView, an enumeration tool in PowerShell Empire, you can search for gMSA accounts and attempt to view password attributes; PowerView’s
Get-DomainGMSAcommand can enumerate gMSA accounts and potentially viewmsDS-ManagedPasswordif you have the necessary permissions.
2.12 Group Policy Object (GPO) Abuse
Group Policy Objects (GPOs) allow administrators to enforce policies and configurations across all domain-connected machines. By modifying a GPO with malicious commands, attackers can achieve privilege escalation or persistence. The effectiveness of this attack lies in the fact that when GPOs are updated—either manually or during regular system updates—these policies are executed on all systems within their scope, including those used by privileged users like administrators. This means that any added malicious task or script will be run with the permissions of all users in that scope, enabling an attacker to execute code as an administrator without direct admin rights.
Guides:
Resources:
Import PowerView
List All GPOs: use PowerView to list all GPOs and check if there are write permissions for any.
Basic GPO Listing
Manual Permission Check: this checks if you have any write permissions on GPOs, which could allow for privilege escalation.
BloodHound Alternative: use BloodHound to check for
WriteGPO,OwnsGPO, orGPO controlprivileges, as they indicate possible GPO manipulation for escalation.
Enumerate a Specific GPO
Identify GPO by Display Name
Convert GPO ID to Name
Check Permissions on Specific GPO: verify if you have edit permissions or ownership on a particular GPO.
Execute the Attack (If Permissions Allow): se
SharpGPOAbuseto manipulate GPOs.Create a Reverse Shell Task
Add User to Administrators Group
Force Policy Update: apply the GPO changes immediately across the domain.
3. 👾 Active Directory Attacking
3.1 AS-REP Roasting
AS-REP Roasting targets accounts that do not require pre-authentication, allowing attackers to request an AS-REP (Authentication Service Response) message containing the encrypted password hash, which can then be brute-forced offline.
How it works:
Attackers request an AS-REP message for accounts that do not enforce Kerberos pre-authentication.
The AS-REP response contains an encrypted portion that uses the user's password hash as a key.
Attackers can extract this hash and crack it offline using tools like
hashcatorJohn the Ripper.
Steps:
Find users without pre-authentication:
AS-REP Roasting using Rubeus:
AS-REP Hash extraction using Impacket:
Crack the AS-REP hash:
3.2 Kerberoasting
Kerberoasting involves attacking Service Principal Names (SPNs) that are configured in Active Directory. Attackers request a Kerberos Ticket-Granting Service (TGS) ticket for these SPNs, extract the service account hash from the ticket, and brute-force the password offline.
How it works:
The attacker requests a TGS for a service account (SPN) that has a valid ticket.
The service's TGS is encrypted with the service account's password hash.
The attacker can extract the TGS ticket and crack it offline using tools like
hashcat.
Steps:
Enumerate Service Principal Names (SPNs):
Request a TGS ticket for SPNs:
Extract TGS ticket from memory using Rubeus:
Crack the TGS hash:
3.3 Silver Tickets
Silver Tickets allow attackers to forge a Ticket-Granting Service (TGS) for specific services like CIFS (file sharing) or HTTP, enabling access to those services without needing a valid TGT from a domain controller.
How it works:
The attacker obtains the NTLM hash or Kerberos hash of a service account.
The attacker uses this hash to create a forged TGS ticket, allowing them to authenticate to specific services (e.g., CIFS, HTTP).
Since Silver Tickets bypass domain controllers, they are harder to detect in logs.
Steps:
Extract NTLM hash of the service account (e.g., CIFS):
Create a Silver Ticket using Mimikatz:
Inject the Silver Ticket into the session:
Access the target service (e.g., CIFS):
3.4 Golden Tickets
Golden Tickets are forged Ticket-Granting Tickets (TGT) that allow attackers to impersonate any user, including Domain Admins, by creating a TGT valid for the entire domain. Golden Tickets are one of the most powerful attacks as they grant persistent, high-level access.
How it works:
The attacker dumps the KRBTGT account hash (using tools like
Mimikatz).Using this hash, they can create a forged TGT for any user.
The forged TGT can be used to authenticate as any user across the domain, including Domain Admins.
Steps:
Dump KRBTGT account hash:
Create Golden Ticket using Mimikatz:
Inject Golden Ticket:
Access domain resources:
3.5 Domain Controller Synchronization (DC Sync)
The DC Sync attack involves mimicking a Domain Controller (DC) to request credentials from another DC, effectively obtaining password hashes (including KRBTGT, Admins) without triggering alarms.
How it works:
Permissions: The attacker needs to have the Replicating Directory Changes or Replicating Directory Changes All permissions, which are often granted to Domain Admins and other high-privilege accounts.
Replication Request: By sending a replication request, the attacker can pull user account data, including password hashes, directly from a Domain Controller.
Credential Theft: Once the attacker obtains these hashes, they can use them for further attacks (like Pass-the-Hash or Pass-the-Ticket) or crack them to obtain plaintext passwords.
Steps:
Identify Domain Admins: ensure you have the required permissions.
Perform DC Sync using Mimikatz:
Extracting all accounts and hashes:
Output to a file:
Crack dumped hashes:
3.6 Cached AD Credentials
Cached credentials allow users to log in to their machines even if the domain controller is unavailable. Attackers can extract these cached credentials from compromised systems.
How it works:
When users log in, the NTLM hash of their password is cached locally.
Attackers can use tools to extract and crack these cached hashes offline.
Steps:
Dump cached credentials using Mimikatz:
Crack cached credentials:
3.7 NTLM Authentication
NTLM (NT LAN Manager) is a challenge-response authentication protocol used in older Windows systems or when Kerberos is unavailable.
How it works:
The client sends a NTLM negotiation message.
The server sends back a challenge (random data).
The client uses the challenge, combined with the user's NTLM hash, to create a response.
The server checks the response using the stored NTLM hash of the user.
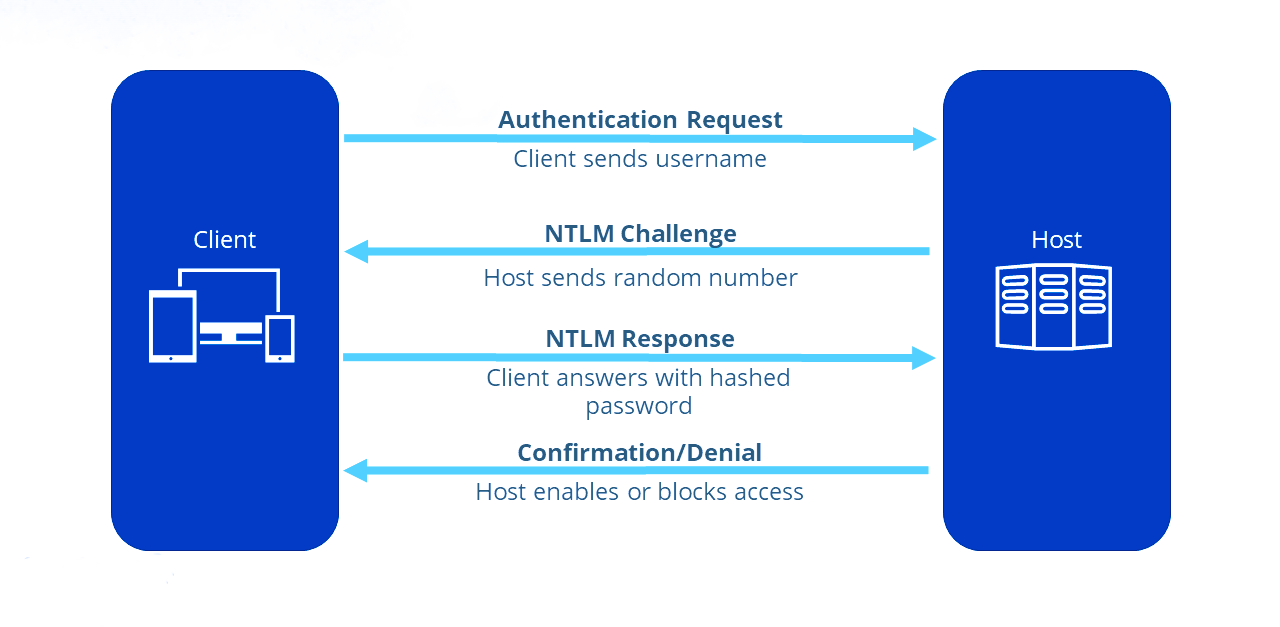
Vulnerabilities:
Pass-the-Hash: Attackers can reuse NTLM hashes without knowing the plaintext password.
NTLM Relay: Attackers can relay NTLM authentication to another server.
Steps to do Pass-the-Hash for AD services:
Dump NTLM hash using Mimikatz:
Pass the NTLM hash using Mimikatz:
Access remote resources:
3.8 Kerberos Authentication
Kerberos is the default authentication protocol in modern Windows domains, offering mutual authentication via tickets.
How it works:
AS-REQ: The client requests a Ticket Granting Ticket (TGT) from the Key Distribution Center (KDC) using their credentials.
AS-REP: The KDC responds with a TGT, encrypted with the user's password hash.
TGS-REQ: The client presents the TGT to the KDC to request access to a service.
TGS-REP: The KDC issues a Ticket Granting Service (TGS) ticket for the requested service.
Service Authentication: The client uses the TGS to authenticate with the target service.
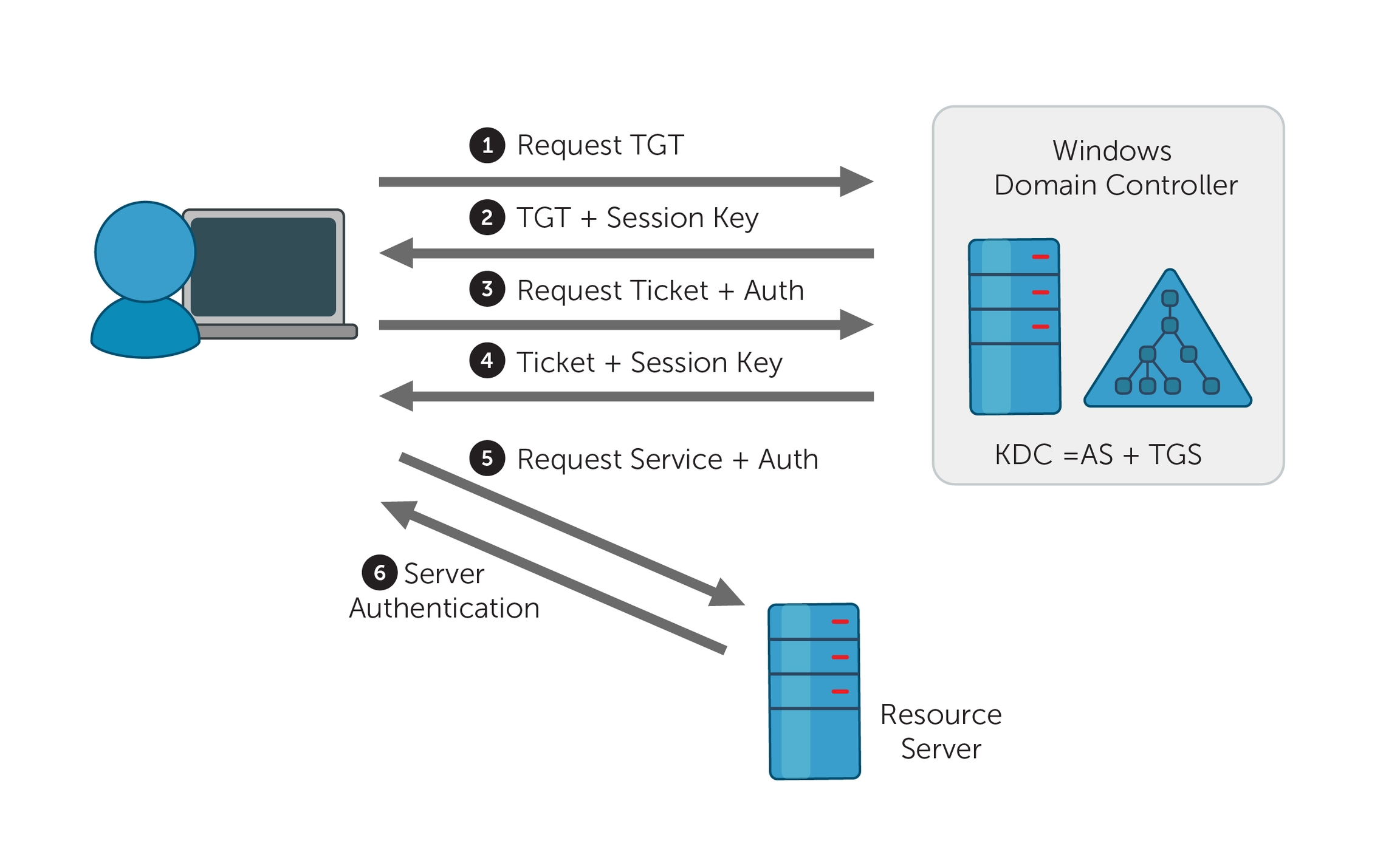
Vulnerabilities:
Pass-the-Ticket: Attackers can steal and reuse Kerberos tickets (TGT or TGS).
Kerberoasting: Attackers extract and crack service account hashes from TGS tickets.
Steps for Pass-the-Ticket Attack:
Dump the TGT ticket using Mimikatz:
Pass the Kerberos TGT ticket:
Access resources:
3.9 Password Attacks
3.9.1 Spraying Creds with Script
3.9.1.1 Running the Script
3.9.1.2 Source Code of the Script
3.9.2. Authenticating using DirectoryEntry
To authenticate against Active Directory using a specific username and password, you can utilize the System.DirectoryServices namespace in PowerShell. Below is an example of how to set this up:
3.9.3 Using CrackMapExec
3.9.3.1 Basic Commands
Basic Check for User Authentication:
Using Kerberos for Authentication:
Domain and SMB Signing Check: checks for SMB signing requirements along with user authentication.
Continue on Error: using the
--continue-on-errorflag will allow the command to run even if some accounts fail.
3.9.3.2 Additional Commands
Attempting to Enumerate Shares on the Target: you can enumerate shared folders on the target machine while testing user credentials.
Testing for SMBv1: to check if the target supports SMBv1.
Getting Session Information: you can obtain active sessions on the target machine.
Dumping SAM Hashes: if you have admin rights, you can attempt to dump the SAM database:
Running Commands Remotely:
3.9.3.3 Possible Services to Test
SMB (Server Message Block) - Port 445
RDP (Remote Desktop Protocol) - Port 3389
WinRM (Windows Remote Management) - Port 5985/5986
HTTP/HTTPS (Web Services) - Ports 80/443
FTP (File Transfer Protocol) - Port 21
Telnet - Port 23
SMTP (Simple Mail Transfer Protocol) - Port 25
DNS (Domain Name System) - Port 53
LDAP (Lightweight Directory Access Protocol) - Ports 389/636
NetBIOS - Ports 137-139
MySQL - Port 3306
PostgreSQL - Port 5432
MS SQL Server - Port 1433
Oracle Database - Port 1521
Redis - Port 6379
Docker Remote API - Port 2375
SNMP (Simple Network Management Protocol) - Port 161
NTP (Network Time Protocol) - Port 123
3.9.4 Using kerbrute
3.10 Shadow Copies
Shadow Copies, also known as Volume Shadow Copy Service (VSS), is a Windows feature that creates backup copies or snapshots of computer files or volumes, even when they are in use. Attackers can exploit Shadow Copies to retrieve sensitive information, including previous versions of files and credentials.
How It Works:
Creation of Shadow Copies: Shadow Copies are created automatically or can be manually initiated. They allow for data recovery and backup without disrupting active processes.
Accessing Shadow Copies: The shadow copies can be accessed through the file system, often found in a hidden directory. This feature can be used to recover deleted files or view past versions of files.
Steps to Attack Shadow Copies:
Create a Shadow Copy of the Entire Disk: this action requires local administrator privileges.
Copy the NTDS Database to the Specified Destination Copying the NTDS Database to the
C:Drive: to back up the NTDS database from the shadow copy, use the following command.
Save the System Registry to the Specified Destination:
Download the Files to the Kali: use strategies from Section 17.
Extract the Data from the NTDS Database using Kali: this command retrieves user credentials and hash values from the NTDS database backup, enabling further security assessments.
(Optional): use Mimikatz to extract the credentials if it is not possible to bring the files to the Kali.
Steps to Access Shadow Copies:
List Shadow Copies: use the following command to view existing shadow copies on a system.
Access a Shadow Copy:
Find the shadow copy you want to access and note its shadow copy ID.
Mount the shadow copy using the following command:
Explore the Mounted Shadow Copy: navigate to the new folder (
C:\ShadowCopy) to explore and extract files.
Recover Sensitive Data: look for sensitive files, such as password files, documents, or configuration files that may contain credentials or sensitive information.
3.11 Constrained Delegation Attack
Constrained Delegation allows specific accounts to impersonate other users and access resources on their behalf, but only for certain services. Attackers can exploit misconfigured constrained delegation to escalate privileges or access sensitive data.
How It Works:
Understanding Delegation: When a service account is set up with constrained delegation, it can request service tickets to access other resources using the identity of the user who authenticated to it.
Exploitation: If an attacker can obtain the service account’s credentials or exploit a misconfiguration, they can impersonate users and access services that the account is permitted to use.
Steps to Exploit a Constrained Delegation Attack:
Identify Delegated Accounts: use the following command to identify accounts with delegated permissions.
Check Constrained Delegation Settings: use the PowerShell command to check for delegated permissions.
Perform Kerberos Ticket Granting: if you have the service account credentials, use them to request service tickets.
Access Resources as a Delegated User: once you have the ticket, access the resources using the identity of the impersonated user.
4. ↔️ Active Directory Lateral Movement
4.1 Techniques and Preparation
PowerShell Execution Policy Bypass:
Having valid credentials: in this case we can use any tools from either Windows or Kali to connect to the system from an internal server, keep in mind the other possibilities of impersonations using Silver and Golden Tickets, they are very important and are in the Section 3, as well as password spraying with
crackmapexecfrom the Section 6.2 and accessing the Shadow Copies (Section 3.10).Pass-the-Ticket: we use a Kerberos ticket to impersonate users, this is done using Silver or Golden Tickets, for that check the Sections 3.3(Silver Ticket) and 3.4 (Golden Ticket).
Overpass-the-Hash: uses an NTLM hash to request a Kerberos ticket (TGT), allowing attacks like pass-the-ticket.
4.2 From Kali
4.2.1 Evil-WinRM
Password:
NTLM Hash:
4.2.2 PsExec
Password:
NTLM Hash:
4.2.3 VMIExec
Password:
NTLM Hash:
4.3 From Windows
4.3.1 DCOM (Distributed Component Object Model)
This technique uses PowerShell's built-in capabilities to execute commands on remote systems via DCOM.
Verify if DCOM is enabled on the target machine.
Use the
Invoke-Commandto Execute Commands via DCOM
(Optional) We can also try to use DCOM via
vmiexec
4.3.2 PsExec
Tool for executing processes on remote systems, particularly useful for obtaining interactive shells.
4.3.3 WinRM
Service that allows remote management of Windows systems through the WS-Management protocol; this is how to establish a remote session:
4.3.4 WinRS
Command-line tool that allows you to run commands on remote systems.
4.3.5 WMIC
Command-line tool to perform Windows Management Instrumentation (WMI) operations, including executing commands remotely.
Last updated